Are your employees equipped to identify and thwart the latest cyber threats? As businesses increasingly rely on digital tools and technology, the importance of ensuring employee cyber resilience cannot be overstated. In today's fast-paced digital landscape, cybercriminals are constantly devising new ways to exploit vulnerabilities and gain unauthorized access to sensitive information. That's where security vulnerability management comes into play, along with testing techniques such as smishing and vishing.
What is Smishing and Vishing?
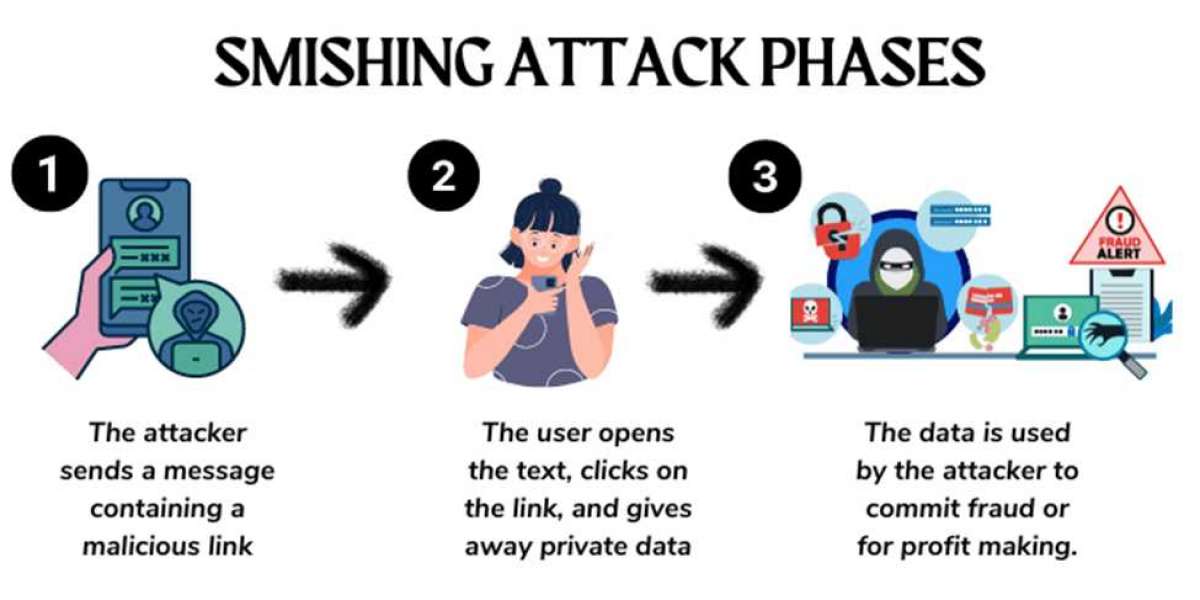
Smishing and vishing are two common tactics used by cybercriminals to trick individuals into divulging sensitive information, such as login credentials or personal data. Smishing, which stands for SMS phishing, involves sending fraudulent text messages that appear to be from legitimate sources, such as banks or government agencies. These messages typically contain urgent requests for personal information or prompt the recipient to click on malicious links.
Vishing, on the other hand, is a form of phishing that utilizes voice calls to deceive individuals. Cybercriminals often pose as trusted entities, such as bank representatives or IT support staff, and use social engineering techniques to extract confidential information over the phone. By leveraging the element of human interaction, vishing attacks can be particularly effective in manipulating unsuspecting victims.
The Role of Security Vulnerability Management
In the face of evolving cyber threats, organizations must adopt a proactive approach to cybersecurity. Security vulnerability management plays a crucial role in identifying, assessing, and mitigating potential security risks within an organization's IT infrastructure. By conducting regular vulnerability scans and assessments, businesses can pinpoint weaknesses in their systems and take corrective action to shore up their defenses.
At Checkmark Security, we specialize in testing the cyber resilience of employees through simulated smishing and vishing attacks. Our team of experts conducts targeted campaigns to assess how well individuals at client organizations adhere to security protocols and respond to suspicious communications. By replicating real-world cyber threats, we help organizations identify gaps in their security posture and bolster their defenses against malicious actors.
Why Employee Training is Essential
In the realm of cybersecurity, employees are often considered the weakest link in the chain. Human error, negligence, or lack of awareness can unwittingly open the door to cyber threats and compromise sensitive data. That's why ongoing training and education are essential components of any comprehensive security strategy.
By empowering employees with the knowledge and skills to recognize and respond to potential threats, organizations can create a human firewall that guards against cyber attacks. Training programs that cover topics such as phishing awareness, social engineering tactics, and best practices for secure communication can help cultivate a culture of vigilance and resilience within the workforce.
Conclusion
As the cybersecurity landscape continues to evolve, organizations must stay vigilant in their efforts to protect against cyber threats. By testing employee cyber resilience through techniques like smishing and vishing, along with implementing robust security vulnerability management practices, businesses can fortify their defenses and mitigate the risk of cyber attacks. Investing in employee training and awareness programs is paramount in building a strong cybersecurity posture that can withstand the challenges of the digital age.